WSO2 Identity Server 5.0.0 or above
travelocity.com web app
First of all we need to know what is travelocity.com web app. travelocity.com web application(.war file) we used to SAML 2.0 authentication and it's related scenario testing purpose with WSO2 IS.
For that we need to download the travelocity.com web app source code and build it using maven. SVN location below,
Replace the whole content with following in pom.xml file,svn co http://svn.wso2.org/repos/wso2/carbon/platform/branches/turing/products/is/5.0.0/modules/samples/sso/
Build using below maven command, for that you need to go download sample /sso directory and run below command,<projectxmlns="http://maven.apache.org/POM/4.0.0"xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 http://maven.apache.org/maven-v4_0_0.xsd"><groupId>org.wso2.identity</groupId><version>5.0.0</version><modelVersion>4.0.0</modelVersion><artifactId>wso2is-identity-samples-sso</artifactId><packaging>pom</packaging><name>Identity Server : SSO Samples</name><modules><module>SSOAgentSample</module></modules></project>
mvn clean install
Go to the /targat directory and copied the travelocity.war file into your [tomcat_home]/webapp directory and restart the tomcat. If your using latest tomcat version no need to restart.Now travelocity.com sample ready for work. Go to browser and type below URL and you can see the travelocity sample app,
http://localhost:8080/travelocity.com/index.jspAfter that you need to start the WSO2 IS 5.0.0 and login as admin with credentials.
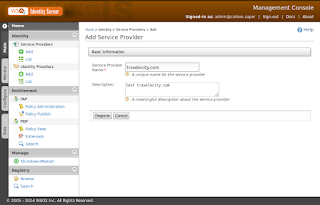
Navigate the main menu and click add under Service Provider. You can see below page.
Click register and then navigate the Inbound Authentication Configuration> SAML web SSO configuration> configure. After you need to configure the below details,
 |
| SP inbound configuration in SAML |
issuer:-
This is the entity id for SAML2 service provider. For this travelocity.com sample issuere is travelocity.com.
Assertion Consumer [ACS] URL:-
Assertion Consumer Service (ACS) URL of the service provider. The identity provider redirects the SAML2 response to this ACS URL.
Use fully qualified username in the NameID:-
checked this as true. A fully qualified username is basically user name with user store domain.
username must be in the following format:
{user store domain}{user name}Enable Response Signing:-
checked this as true. This is used to sign the SAML2 Responses returned after the authentication process is complete.
Enable Attribute Profile:-
The Identity Server supports a basic attribute profile and it mean basic user information such as username,email,sex,telephone number. The identity provider can include the user’s attributes in the SAML Assertions as an attribute statement.
After completed this details click update. Then you can used above travelocity.com URL for test this.You can see the travelocity.com home page below,
 |
| travelocity home page |
https://addons.mozilla.org/en-US/firefox/addon/saml-tracer/After installation complete you can run the saml-tracer by navigating the tool>SAML Tracer.
Just click the below link in travelocity.com homepage,
Meanwhile redirect to the WSO2 IS login page. Login with admin credentials. By default both user name & password is "admin".
After login it redirect to the travelocity.com page as below,
If you start saml-tracer before login to the IS you can trace SAML as below, Here last POST response create the SAML2 assertion for travelocity.com issuer.
 |
| saml-tracer |

No comments:
Post a Comment